ARTICLE AD BOX
WooCommerce published an advisory astir an XSS vulnerability portion Wordfence simultaneously advised astir a captious vulnerability successful a WooCommerce plugin named Dokan Pro. The advisory astir Dokan Pro warned that a SQL Injection vulnerability allows unauthenticated attackers to extract delicate accusation from a website database.
Dokan Pro WordPress Plugin
The Dokan Pro plugin allows idiosyncratic to alteration their WooCommerce website into a multi-vendor marketplace akin to sites similar Amazon and Etsy. It presently has implicit 50,000 installations Plugin versions up to and including 3.10.3 are vulnerable.
According to WordFence, mentation 3.11.0 represents the afloat patched and safest version.
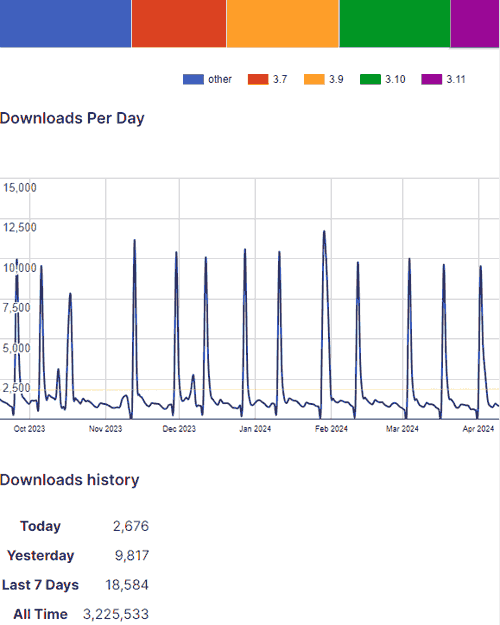
WordPress.org lists the existent fig of plugin installations of the lite mentation astatine implicit 50,000 and a full all-time fig of installations of implicit 3 million. As of this infinitesimal lone 30.6% of installations were utilizing the astir up to day version, 3.11 which whitethorn mean that 69.4% of each Dokan Pro plugins are vulnerable.
Screenshot Of Dokan Plugin Download Statistics
Changelog Doesn’t Show Vulnerability Patch
The changelog is what tells users of a plugin what’s contained successful an update. Most plugin and taxable makers volition people a wide announcement that an update contains a vulnerability patch. According to Wordfence, the vulnerability affects versions up to and including version 3.10.3. But the changelog notation for mentation 3.10.4 that was released Apr 25, 2024 (which is expected to beryllium patched) does not amusement that there’s a patch. It’s imaginable that the steadfast of Dokan Pro and Dokan Lite didn’t privation to alert hackers to the captious vulnerability.
Screenshot Of Dokan Pro Changelog

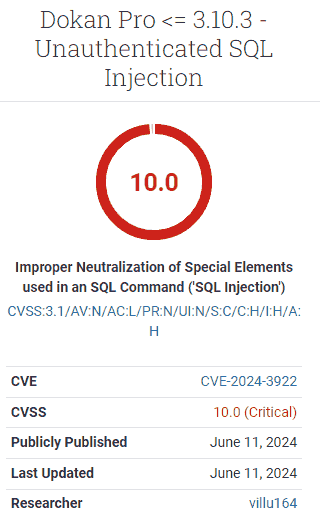
CVSS Score 10
The Common Vulnerability Scoring System (CVSS) is an unfastened modular for assigning a people that represents the severity of a vulnerability. The severity people is based connected however exploitable it is, the interaction of it, positive supplemental metrics specified arsenic information and urgency which unneurotic adhd up to a full people from slightest terrible (1) to the highest severity (10).
The Dokan Pro plugin received a CVSS people of 10, the highest level severity, which means that immoderate users of the plugin are recommended to instrumentality contiguous action.
Screenshot Of Dokan Pro Vulnerability Severity Score
Description Of Vulnerability
Dokan Pro was recovered to incorporate an Unauthenticated SQL Injection vulnerability. There are authenticated and unauthenticated vulnerabilities. Unauthenticated means that an attacker does not request to get idiosyncratic credentials successful bid to motorboat an attack. Between the 2 kinds of vulnerabilities, unauthenticated is the worst lawsuit scenario.
A WordPress SQL Injection vulnerability is 1 successful which a plugin oregon taxable allows an attacker to manipulate the database. The database is the bosom of each WordPress website, wherever each password, login names, posts, themes and plugin data. A vulnerability that allows anyone to manipulate the database is considerably terrible – this is truly bad.
This is however Wordfence describes it:
“The Dokan Pro plugin for WordPress is susceptible to SQL Injection via the ‘code’ parameter successful each versions up to, and including, 3.10.3 owed to insufficient escaping connected the idiosyncratic supplied parameter and deficiency of capable mentation connected the existing SQL query. This makes it imaginable for unauthenticated attackers to append further SQL queries into already existing queries that tin beryllium utilized to extract delicate accusation from the database.”
Recommended Action For Dokan Pro Users
Users of the Dokan Pro plugin are recommended to see updating their sites arsenic soon arsenic possible. It’s ever prudent to trial updates earlier their uploaded unrecorded to a website. But owed to the severity of this vulnerability, users should see expediting this update.
WooCommerce published an advisory of a vulnerability that affects versions 8.8.0 and higher. The vulnerability is rated 5.4 which is simply a mean level threat, and lone affects users who person the Order Attribute diagnostic enabled activated. Nevertheless, WooCommerce “strongly” recommends users update arsenic soon arsenic imaginable to the astir existent mentation (as of this writing), WooCommerce 8.9.3.
WooCommerce Cross Site Scripting (XSS) Vulnerability
The benignant of vulnerability that affects WooCommerce is called Cross Site Scripting (XSS) which is simply a benignant of vulnerability that depends connected a idiosyncratic (like a WooCommerce store admin) to click a link.
According to WooCommerce:
“This vulnerability could let for cross-site scripting, a benignant of onslaught successful which a atrocious histrion manipulates a nexus to see malicious contented (via codification specified arsenic JavaScript) connected a page. This could impact anyone who clicks connected the link, including a customer, the merchant, oregon a store admin.
…We are not alert of immoderate exploits of this vulnerability. The contented was primitively recovered done Automattic’s proactive information probe programme with HackerOne. Our enactment teams person received nary reports of it being exploited and our engineering squad analyses did not uncover it had been exploited.”
Should Web Hosts Be More Proactive?
Web developer and hunt selling adept Adam J. Humphreys, Of Making 8, inc. (LinkedIn profile), feels that web hosts should beryllium much proactive astir patching captious vulnerabilities, adjacent though that whitethorn origin immoderate sites to suffer functionality if there’s a struggle with immoderate different plugin oregon taxable successful use.
Adam observed:
“The deeper contented is the information that WordPress remains without car updates and a changeless vulnerability which is the illusion their sites are safe. Most halfway updates are not performed by hosts and astir each azygous big doesn’t execute immoderate plugin updates adjacent if they bash them until a halfway update is performed. Then determination is the information astir premium plugin updates volition often not execute automatically. Many of which incorporate captious information patches.”
I asked if helium meant a propulsion update, wherever an update is forced onto a website.
“Correct, galore hosts volition not execute updates until a WordPress halfway update. Softaculous engineers confirmed this for me. WPEngine which claims afloat managed updates doesn’t bash it connected the frequence to spot successful a timely manner for said plugins. WordPress without ongoing absorption is simply a vulnerability and yet fractional of each websites are made with it. This is an oversight by WordPress that should beryllium addressed, successful my opinion.”
Read much astatine Wordfence:
Dokan Pro <= 3.10.3 – Unauthenticated SQL Injection
Read the authoritative WooCommerce vulnerability documentation:
WooCommerce Updated to Address Cross-site Scripting Vulnerability
Featured Image by Shutterstock/New Africa


![Win Higher-Quality Links: The PR Approach To SEO Success [Webinar] via @sejournal, @lorenbaker](https://www.searchenginejournal.com/wp-content/uploads/2025/03/featured-1-716.png)



 English (US)
English (US)