ARTICLE AD BOX
A vulnerability advisory was issued astir 2 WordPress themes recovered connected ThemeForest that could let a hacker to delete arbitrary files and inject malicious scripts into a website.
Two WordPress Themes Sold On ThemeForest
The 2 WordPress themes with vulnerabilities are sold connected ThemeForest and unneurotic they person implicit a fractional cardinal sales.
The 2 themes are:
- Betheme taxable for WordPress (306,362 sales)
- The Enfold – Responsive Multi-Purpose Theme for WordPress (260,607 sales)
Betheme Theme for WordPress Vulnerability
Wordfence issued an advisory that The Betheme taxable contained a PHP Object Injection vulnerability that was rated arsenic a precocious threat.
Wordfence was discreet successful their statement of the vulnerability and offered nary details of the circumstantial flaw. However, successful the discourse of a WordPress theme, a PHP Object Injection vulnerability usually arises erstwhile a idiosyncratic input is not decently filtered (sanitized) for unwanted uploads and inputs.
This is however Wordfence described it:
“The Betheme taxable for WordPress is susceptible to PHP Object Injection successful each versions up to, and including, 27.5.6 via deserialization of untrusted input of the ‘mfn-page-items’ station meta value. This makes it imaginable for authenticated attackers, with contributor-level entree and above, to inject a PHP Object. No known POP concatenation is contiguous successful the susceptible plugin.
If a POP concatenation is contiguous via an further plugin oregon taxable installed connected the people system, it could let the attacker to delete arbitrary files, retrieve delicate data, oregon execute code.”
Has Betheme Theme Been Patched?
Betheme Theme for WordPress has received a spot connected August 30, 2024. But Wordfence’s advisory isn’t acknowledging it. It’s imaginable that the advisory needs to beryllium updated, not sure. Nevertheless, it’s recommended that users of the Enfold taxable see updating their taxable to the newest version, which is Version 27.5.7.1.
The Enfold – Responsive Multi-Purpose Theme for WordPress
The Enfold Responsive Multi-Purpose WordPress taxable contains a antithetic flaw and was fixed a little severity standing of 6.4. That said, the steadfast of the taxable has not issued a hole for the vulnerability.
A Stored Cross-Site Scripting (XSS) was discovered successful the WordPress taxable from a flaw originating successful a nonaccomplishment to sanitize inputs.
Wordfence describes the vulnerability:
“The Enfold – Responsive Multi-Purpose Theme taxable for WordPress is susceptible to Stored Cross-Site Scripting via the ‘wrapper_class’ and ‘class’ parameters successful each versions up to, and including, 6.0.3 owed to insufficient input sanitization and output escaping. This makes it imaginable for authenticated attackers, with Contributor-level entree and above, to inject arbitrary web scripts successful pages that volition execute whenever a idiosyncratic accesses an injected page.”
Enfold Vulnerability Has Not Been Patched
The Enfold – Responsive Multi-Purpose Theme for WordPress has not been patched arsenic of this penning and remains vulnerable. The changelog documenting the updates to the taxable shows that it was past updated successful August 19, 2024.
Screenshot Of Enfold WordPress Theme’s Changelog
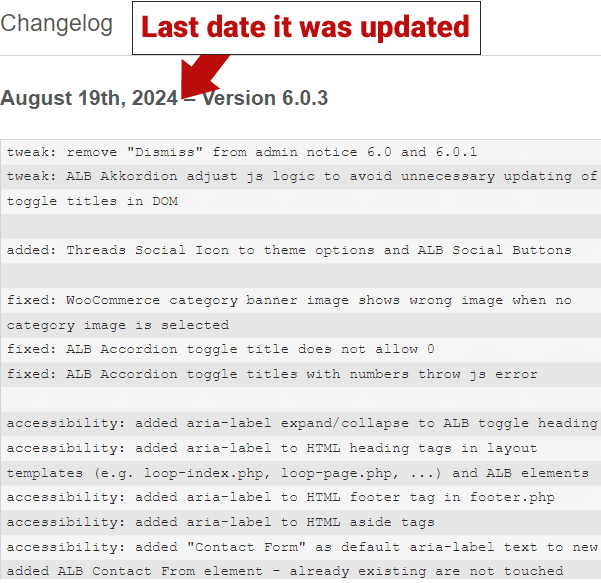
The Enfold – Responsive Multi-Purpose Theme for WordPress has not been patched arsenic of this penning and remains vulnerable.
Wordfence’s advisory warned:
“No known spot available. Please reappraisal the vulnerability’s details successful extent and employment mitigations based connected your organization’s hazard tolerance. It whitethorn beryllium champion to uninstall the affected bundle and find a replacement.”
Read the advisories:
Betheme <= 27.5.6 – Authenticated (Contributor+) PHP Object Injection


![Win Higher-Quality Links: The PR Approach To SEO Success [Webinar] via @sejournal, @lorenbaker](https://www.searchenginejournal.com/wp-content/uploads/2025/03/featured-1-716.png)



 English (US)
English (US)