ARTICLE AD BOX
What Is Data Strategy?
A information strategy is simply a broad program for handling an organization's data. It outlines technology, processes, and rules to negociate information effectively. It besides provides wide guidelines for acquiring, storing, distributing, and utilizing data.
Why is this necessary?
Because businesses of each sizes cod and nutrient immense amounts of earthy data.
An estimated 181 zettabytes of data volition beryllium generated worldwide by 2025. To enactment that into perspective, 1 zettabyte is astir the equivalent of streaming Netflix continuously for 36 cardinal years.
That’s a batch of data.
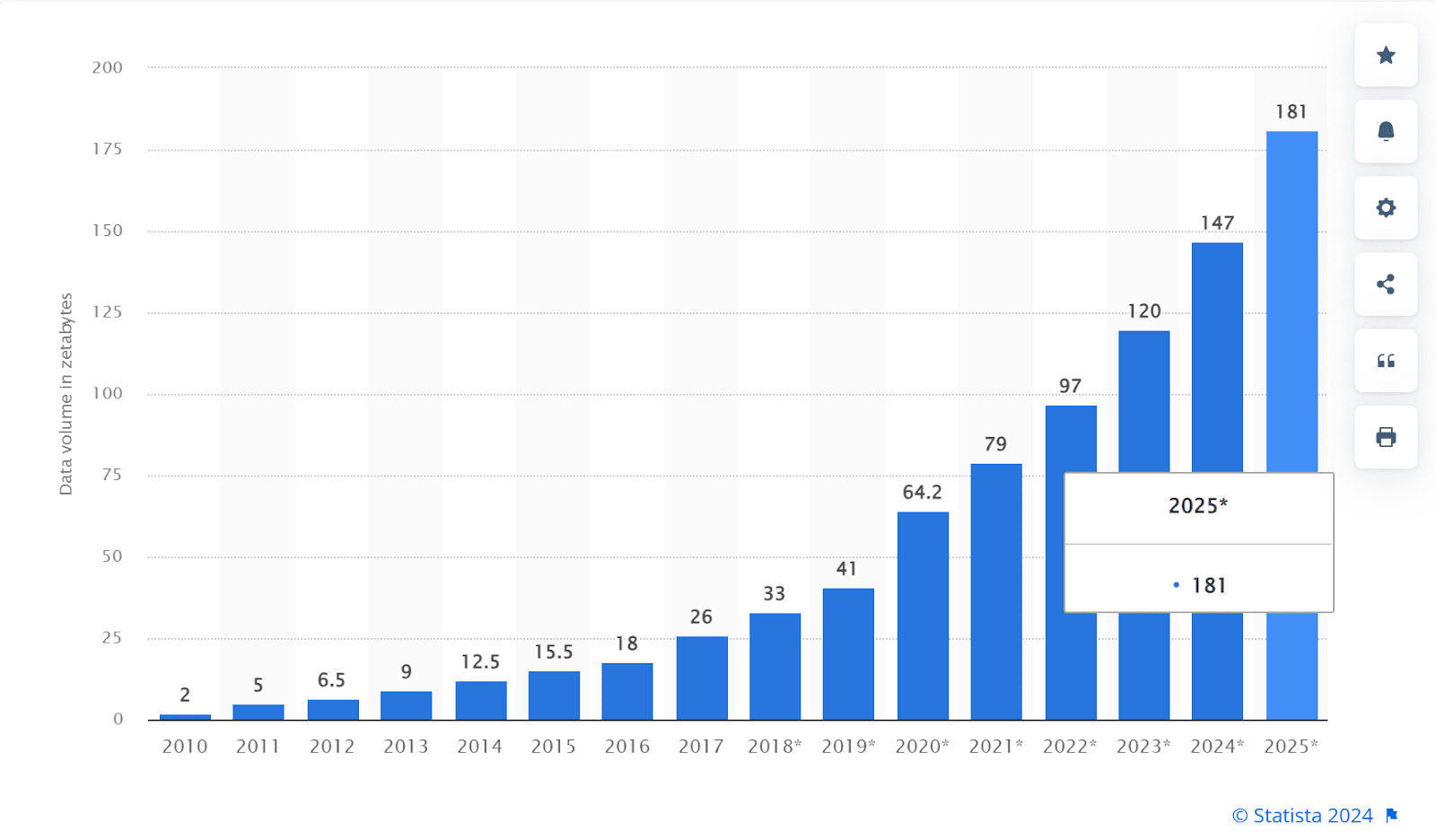
Image Source: Statista
Managing each this data, keeping it unafraid and compliant, and utilizing it to thrust concern worth tin beryllium challenging.
After all, information is lone utile if you tin really usage it. Unfortunately, galore businesses acquisition issues similar silos and duplicates, and incomplete, inaccurate, oregon obsolete data. Or, adjacent worse, a information breach.
Creating a information strategy addresses these issues (and more) truthful businesses tin usage their information successful meaningful ways and summation a competitory advantage.
Further reading: What Is Data-Driven Marketing, and Why Is It Important?
What Are the Benefits of a Data Strategy?
A coagulated information strategy program is indispensable for astir businesses today. Let’s research the cardinal benefits:
Smarter Decision-Making
Analyzing trends and insights enables companies to recognize what’s working, what’s not, and what could happen. This helps them marque smarter, faster decisions.
To marque much informed decisions, a company’s information strategy mightiness see the pursuing fashionable analytics model. It has 3 cardinal elements: descriptive, diagnostic, and predictive analytics.
Descriptive Analytics
Descriptive analytics involves analyzing humanities information to recognize what has happened successful the past.
For example, a institution mightiness usage Excel oregon Google Sheets to reappraisal income information and place seasonal changes. Or they mightiness look astatine rival data, similar the fig of visitors and postulation sources, utilizing Semrush’s Traffic Analytics.
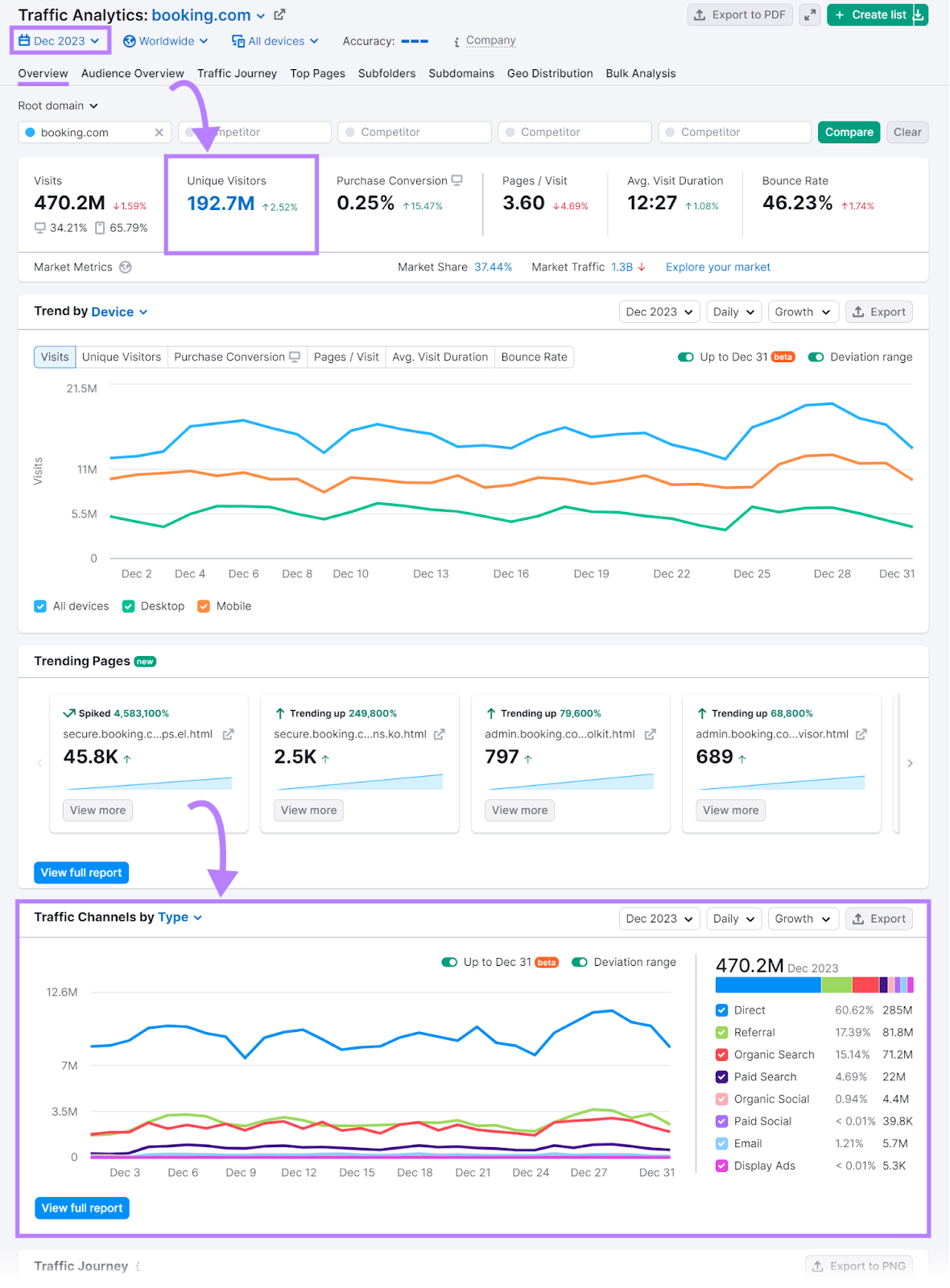
Further reading: What Is a Competitive Analysis and How Do You Conduct One?
Diagnostic Analytics
This benignant of analytics delves into the reasons down past events.
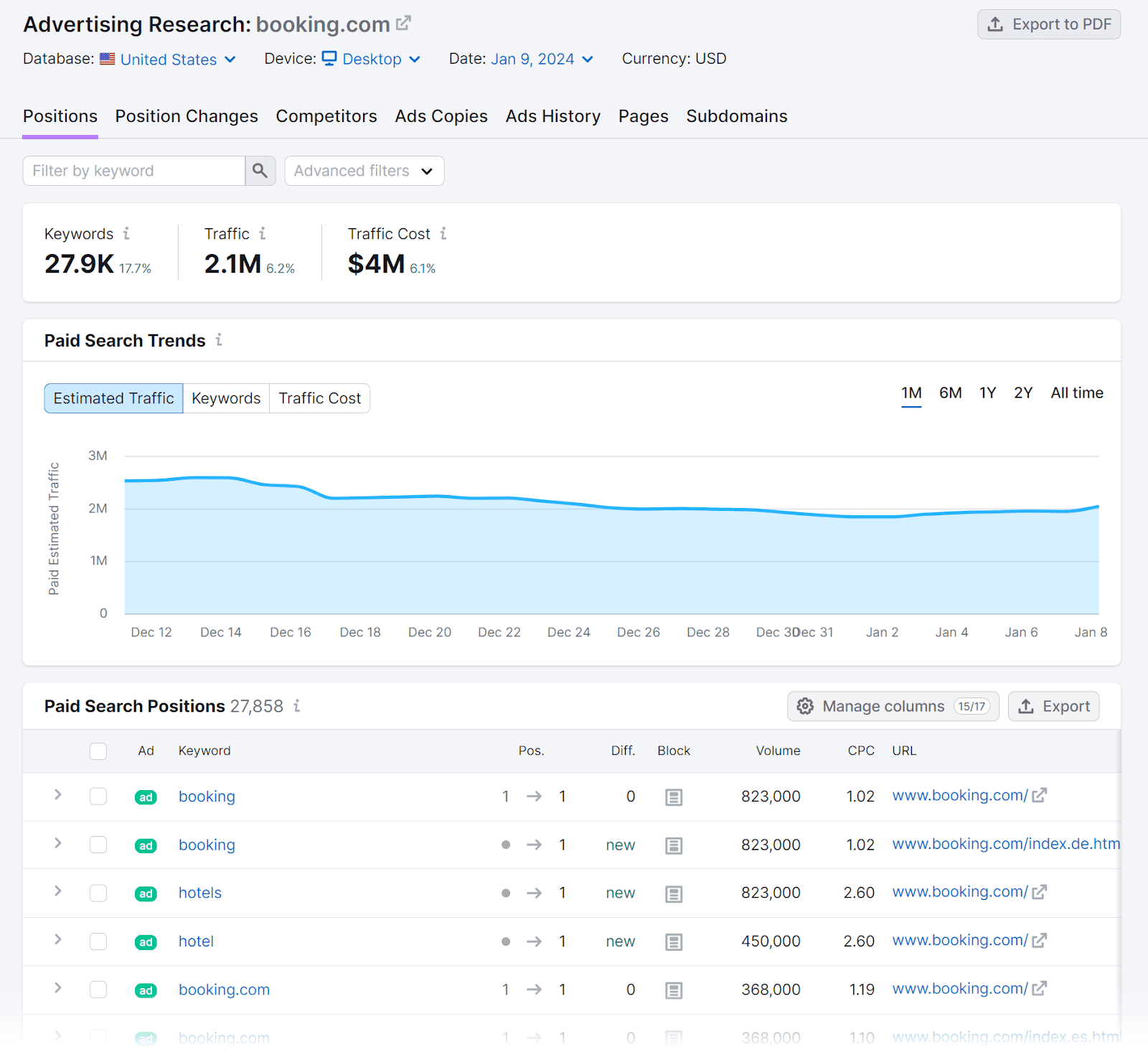
Let’s accidental you announcement immoderate changes successful your Google Ads show and privation to fig retired wherefore they’re happening.
Our Advertising Research instrumentality tin assistance you show your rivals' pay-per-click (PPC) activities, including their advertisement walk and advertisement copy. You tin usage these insights to place competitory trends and strategies that mightiness power your advertisement performance.
Predictive Analytics
Predictive analytics forecasts aboriginal events based connected what has happened before.
This usually requires precocious statistical investigation and artificial quality (AI) oregon instrumentality learning (ML) technology.
Historical insights and aboriginal predictions alteration the institution to expect caller trends and tailor its merchandise improvement and selling efforts.
Better Customer Experience
Data helps businesses recognize how, when, wherever and what their customers similar to buy. And what makes them tick.
Brands tin usage lawsuit information to:
- Personalize cardinal touchpoints, similar the website and lawsuit work channels
- Optimize products and experiences
- Do a amended occupation of gathering lawsuit needs
For example, brands tin email customers erstwhile their favourite merchandise comes backmost successful banal oregon they’re owed for a refill. Like favored nutrient marque Chewy does here:
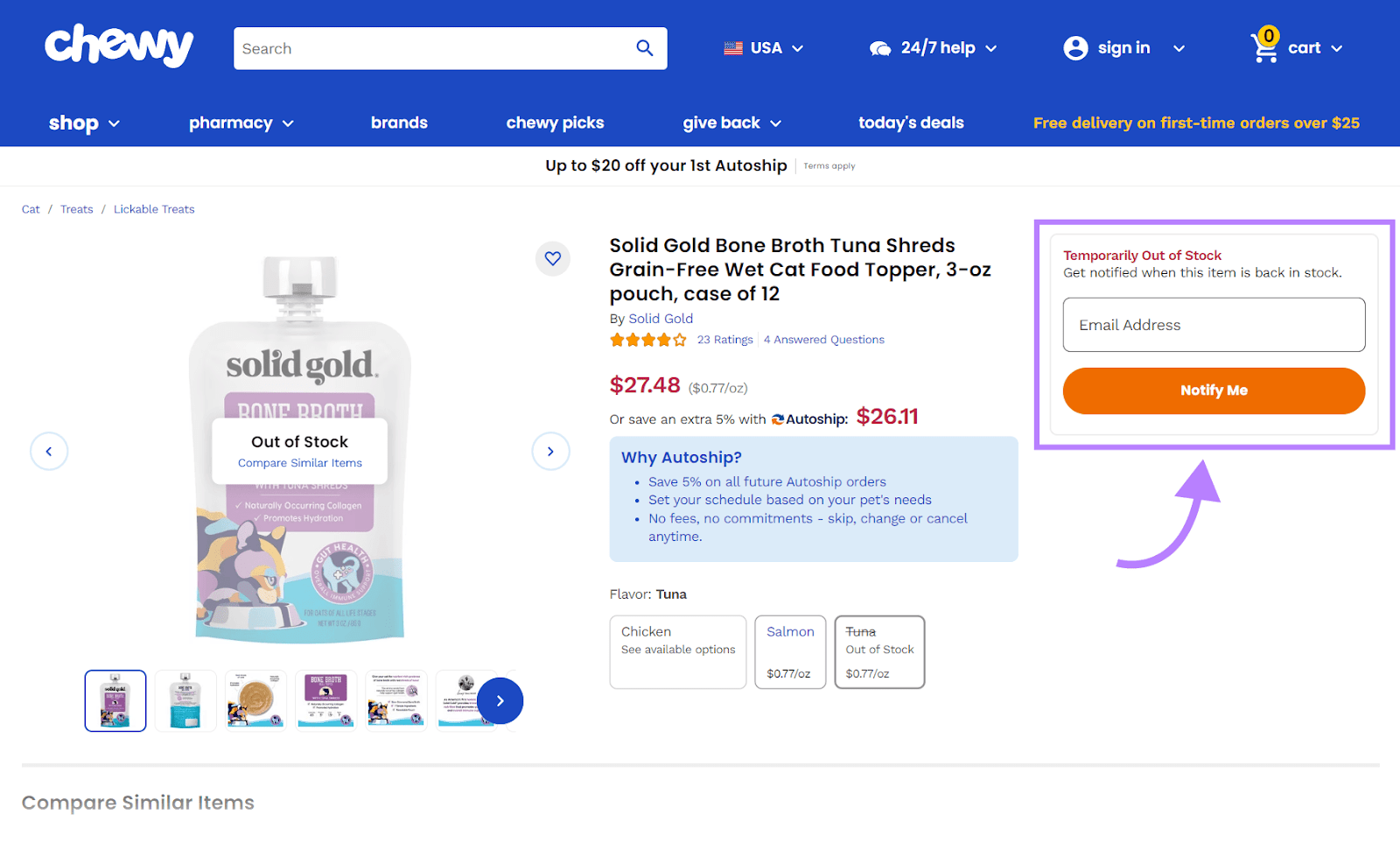
This helps boost lawsuit loyalty and debar missed sales.
Improved Data Compliance and Security
Brands grip ample amounts of confidential lawsuit data. Like names, addresses, and recognition paper information.
For example, let’s accidental you’re a regular shopper astatine Target and privation to motion up for peculiar deals and a day gift. They inquire you for idiosyncratic information, including your name, email address, and telephone number.

Brands person a work to their customers to support these details safe.
Dropping the shot connected privateness and information tin outgo businesses a batch of clip and money. According to IBM research, the planetary mean outgo of a information breach was $4.45 million.
Unfortunately, information hacks and cybersecurity incidents hap each the time. In fact, the aforesaid IBM probe showed that 51% of organizations planned to amended information owed to a breach.
A coagulated strategy helps businesses store and negociate lawsuit information securely truthful lone authorized radical tin entree it—for the intended purpose.
Increased Efficiency and Reduced Costs
Data tin radiance a spotlight connected areas wherever businesses request to improve.
So they can:
- Optimize workflows
- Improve budgeting
- Adjust assets allocation
- Save costs
What’s more, a information strategy tin assistance businesses spot opportunities, similar caller gross streams and concern models. Which tin further trim costs and thrust revenue.
Adoption of Advanced Technologies
Organizations that usage information AI and automation prevention $1.76 million compared to those that don’t. But to leverage these solutions and summation the benefits, businesses request clean, accurate, accessible data.
Advanced technologies similar AI and ML usage important amounts of data. A information strategy helps guarantee information meets the required prime standards truthful businesses tin follow caller technologies and information models with confidence.
Types of Data Strategy
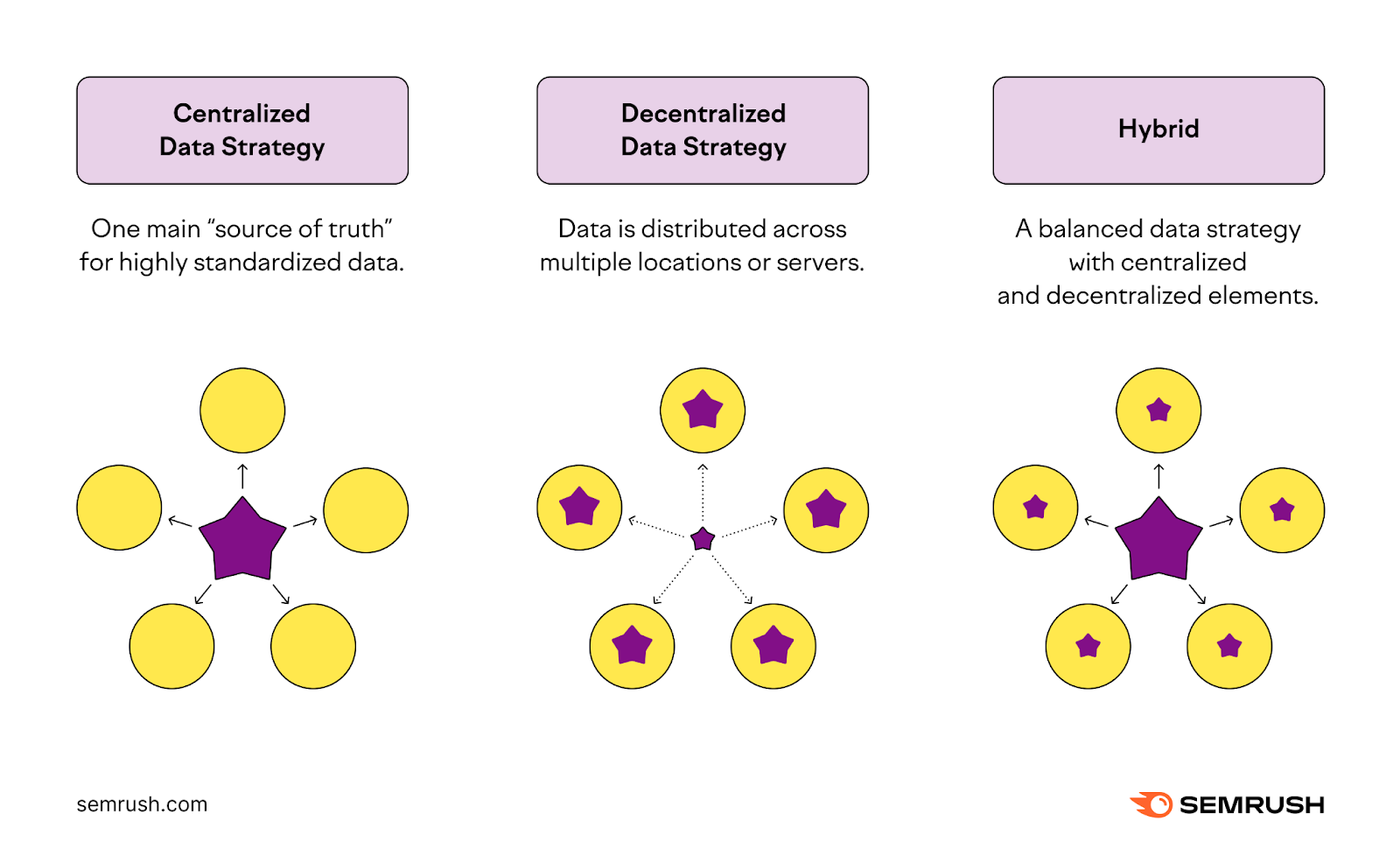
Organizations tin follow antithetic information strategies based connected their needs: centralized, decentralized, oregon hybrid.
Centralized Data Strategy
A centralized attack to information strategy involves 1 main “source of truth.” A single, cardinal repository collects and stores information from aggregate sources, similar lawsuit feedback and income transaction records.
This attack ensures standardization and consistency of captious information similar revenue, customer, and income information.
This is particularly beneficial for ample organizations that indispensable support uniformity crossed antithetic departments.
Why?
So everyone works with the same, reliable information for show appraisal and decision-making.
Decentralized Data Strategy
A decentralized information strategy offers flexibility, with information distributed crossed aggregate locations oregon servers. This attack suits organizations operating successful a fast-changing situation oregon with autarkic departments with antithetic information needs.
For instance, a startup with antithetic task teams mightiness similar this for scalability and to debar a azygous constituent of failure—meaning if 1 information root goes down, others stay functional, ensuring continuous information access.
Hybrid Data Strategy
A hybrid information strategy combines centralized and decentralized approaches.
For example, successful a institution utilizing a hybrid approach, the concern and selling departments mightiness trust connected centralized information for creating monthly show reports. This is the centralized aspect. Meanwhile, the concern section mightiness besides incorporated circumstantial fiscal information exclusive to them. This is decentralized.
A balanced attack lets companies support a azygous root of information for overarching concern metrics. At the aforesaid time, idiosyncratic departments person the flexibility to usage and negociate information successful ways astir suited to their circumstantial functions.
This strategy is perfect for mean to ample companies requiring some company-wide consistency and department-specific agility successful information handling.
Overall, the prime of information strategy depends connected the company's size, structure, industry, and needs.
Further reading: 6 Types of Reports for Making Data-Driven Decisions
Data Strategy Framework
Before gathering a information strategy, it’s important to recognize what a information strategy consists of. Your information strategy model should see the pursuing indispensable information strategy components:
Data Governance
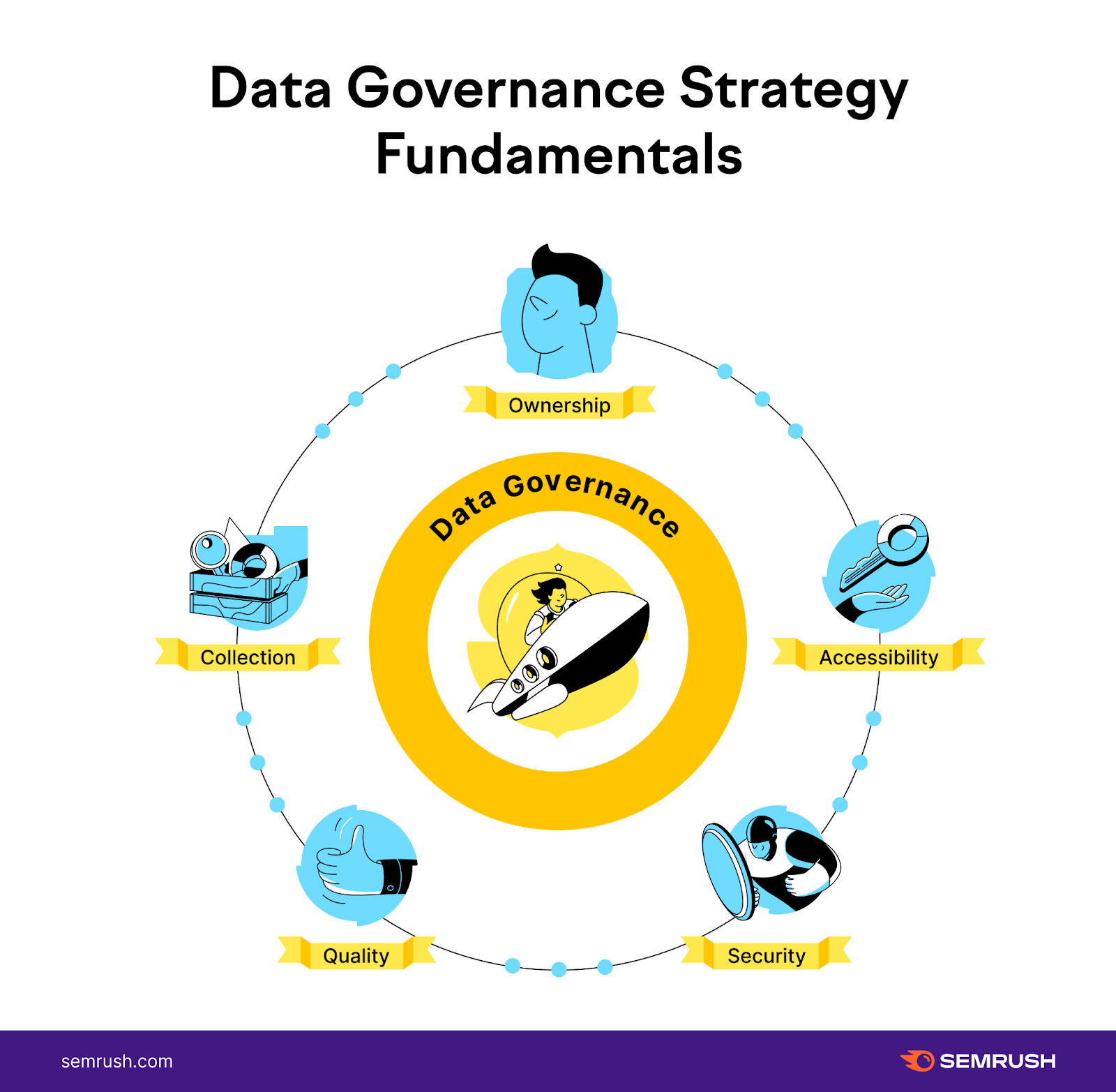
Data governance involves establishing rules, policies, and standards to guarantee information crossed the enactment is secure, accurate, and compliant. It determines what benignant of information is collected and how. And it clarifies information ownership and who has entree to what.
Data Quality
Data prime evaluates a company’s information based connected factors like:
- Accuracy
- Completeness
- Consistency
- Reliability
- Freshness
Assessing information prime helps organizations spot immoderate errors oregon issues and find whether the information successful their systems is acceptable to service its intended purpose.
Data prime is important. According to Gartner, mediocre information prime costs organizations $12.9 cardinal per twelvemonth connected average.
To find the prime of their data, organizations tin inventory their information assets and execute baseline studies to measurement the accuracy, uniqueness and validity of selected information sets. Data absorption tools tin assistance with this.
Data Architecture
Data architecture refers to the wide operation and setup of an organization's information ecosystem. This includes the plan of databases and immoderate different tools utilized to store oregon negociate data. Like information warehouses (central repositories of information) and unreality platforms (online information retention solutions).
Data architecture aims to guarantee that the information infrastructure supports the organization’s requirements successful presumption of performance, scalability, and reliability.
For instance, see a fast-growing startup. As the concern scales, its information needs volition besides evolve. Initially, a tiny database mightiness beryllium sufficient. However, arsenic the institution grows, this basal setup astir apt won’t beryllium capable to grip the accrued measurement and complexity of data.
Data Compliance
Data compliance ensures an organization's handling of information is successful enactment with applicable information extortion laws and regulations.
Almost each concern collects astatine slightest immoderate information connected its customers. Even if it’s conscionable website cookies and email addresses, similar this:
Companies are legally obligated to support lawsuit information harmless and usage it fairly, which is wherever privateness laws travel in.
Privacy laws acceptable wide expectations for however companies should grip people's idiosyncratic information. They archer businesses what they tin and can't bash with the information they collect—like not sharing it with 3rd parties without permission. Failure to comply tin pb to dense fines.
The laws you request to travel volition beryllium connected wherever your institution is based and wherever you bash business.
For example, if you run wrong the European Union oregon grip information from EU citizens, you apt indispensable comply with the GDPR (General Data Protection Regulation). Similarly, if your concern activities impact the authorities of California successful the U.S., the CCPA (California Consumer Privacy Act) apt applies.
Data Security
Data information is the signifier of protecting information from unauthorized access. Like ransomware hacks and different cybersecurity threats.
Data information includes elements like:
- Encryption: Converting information into a coded format to forestall unauthorized access
- Access control: Setting idiosyncratic permissions to restrict information entree to authorized individuals only
- Regular audits: Conducting checks to place vulnerabilities and update information measures
- Employee training: Educating unit connected however to debar communal cyber threats, similar phishing emails
- Incident effect planning: Preparing a wide program connected what to bash successful the lawsuit of a information breach
Data Operations
Data operations screen the day-to-day absorption of data. This includes information processing, backup, recovery, and maintenance.
Efficient information operations guarantee that information is ever disposable and reliable, supporting ongoing concern activities and decision-making processes.
Analytics and Reporting
Analytics and reporting alteration earthy information into meaningful insights. This involves information analytics platforms to analyse information and make reports to pass concern strategies.
Analytics is important due to the fact that it enables organizations to crook their information into insights. So they tin place trends, patterns, and opportunities. Such arsenic which products are the astir popular, which selling channels are astir effective, and which markets they should absorption connected oregon grow into.
Data Culture and Literacy
Typically, a institution collects information connected 2 groups of people: employees and customers. Both groups should cognize what benignant of information the institution collects, why, and however it is stored and processed.
Customers request to beryllium definite you are handling their information successful a unafraid and compliant way. And that accusation needs to beryllium transparent. For example, Semrush’s information information policy is disposable connected the institution website.
Educating and engaging employees is cardinal to leveraging information effectively. A data-driven civilization encourages a mindset wherever employees usage information to usher their decisions, starring to improved concern performance.
How to Build a Data Strategy successful 7 Steps
Now you recognize which components of a information strategy are important, you’re acceptable to make your information strategy. The pursuing information strategy champion practices volition assistance you bash conscionable that.
1. Align with Key Stakeholders
Key stakeholders, similar IT and concern leaders, are captious successful providing the indispensable insights and buy-in to enactment a information strategy. Their engagement helps guarantee the strategy aligns with concern needs and expectations.
To recognize their priorities and symptom points, you tin inquire them questions like:
- What are your main concern goals and initiatives that necessitate information and AI?
- What are your biggest challenges erstwhile it comes to achieving those priorities?
- What bash you privation you could usage information for that you can’t close now?
2. Define Clear Objectives and Use Cases
Clear objectives and factual usage cases supply absorption and intent to the information strategy.
Objectives should beryllium intimately aligned with wide business goals. Such arsenic expanding marketplace share, improving lawsuit satisfaction, and driving operational efficiency.
Then, you tin drill down into cardinal uses to recognize however antithetic departments and teams usage data, what types of information are astir invaluable to them, and the outcomes they would similar to achieve.
Potential usage cases could include:
- Increase lawsuit loyalty done personalized selling strategies
- Optimize inventory and proviso concatenation management
- Drive merchandise innovation by analyzing lawsuit feedback
- Improve fiscal show done outgo reduction
- Improve lawsuit work by analyzing lawsuit interactions
3. Conduct a Data Audit
Evaluate your existing information infrastructure, tools, and processes. This thorough audit should place however you presently collect, store, process, and usage information successful your organization.
Here’s however you tin bash that:
- Data inventory: Begin by cataloging each information sources wrong your organization. Tools similar Apache Atlas and Alation tin assistance successful mapping and knowing your information landscape.
- Data prime assessment: Use information prime tools specified arsenic Informatica oregon Talend to measure your data's accuracy, consistency, and completeness. This measurement is captious for identifying information prime issues that could interaction analytics.
- Infrastructure evaluation: Review your information storage, processing, and absorption systems. Tools similar AWS Well-Architected Tool and Microsoft Azure's Advisor tin connection insights into the ratio and information of your unreality infrastructure.
- Process analysis: Examine your information collection, storage, and utilization processes.Process mining tools similar Celonis and Signavio tin place inefficiencies oregon bottlenecks successful your information workflows.
4. Develop Data Governance Policies
Now, it’s clip to make information governance policies to specify information ownership, roles, responsibilities, and procedures.
Start by consulting with the cardinal stakeholders defined successful measurement one. This collaborative attack ensures that your policies are aligned with assorted concern objectives.
Here are immoderate cardinal policies you are apt to need:
- Data ownership: Defines who owns assorted information assets wrong the organization
- Data quality: Establishes standards for accuracy, completeness, and reliability of data
- Data entree and control: Outlines who tin entree data, nether what conditions, and with what level of authority
- Data privateness and protection: Includes guidelines for protecting delicate information and complying with privateness laws
- Data retention Determines however agelong information is kept and however it is archived oregon disposed of
- Data usage: Sets rules for the due usage of information wrong the organization, including however and erstwhile it tin beryllium shared
5. Develop an Implementation Plan
With your information governance policies defined, the adjacent measurement is to crook these policies into action. That’s wherever a broad implementation program comes in. It serves arsenic a roadmap to assistance you execute your information strategy.
Here’s what you’ll request to do:
- Write down and stock the policies: Most businesses person interior policies (for employees) and outer policies (for the wide public). Consider how, when, and wherever to people and administer this information. For example, you whitethorn request to adhd a privateness argumentation to your website.
- Identify required changes: Based connected the information audit, fig outwhat changes are indispensable to align with the caller policies. This could see upgrading technology, modifying information processes, oregon introducing caller information absorption practices.
- Allocate resources: Determine the resources needed for implementation, including personnel, technology, and budget. Ensure that these resources are allocated appropriately to enactment the execution of the plan.
6. Educate Employees
For a information strategy to succeed, each employees indispensable recognize its value and beryllium alert of changes. Effective acquisition and connection are essential.
Here’s however to amended employees:
- Assess grooming needs: Figure retired however antithetic departments and roles usage information and what they request to know
- Create a grooming program: A structured grooming programme should see information strategy essentials, similar governance, policies, and the interaction connected employees’ regular tasks
- Leverage interior platforms: If your institution is utilizing Slack, for example, you tin make a information governance transmission wherever employees tin inquire questions, stock insights, and entree cardinal resources
This helps employees get up to velocity with the information strategy and each applicable policies.
7. Continuously Monitor and Refine Your Data Strategy
Finally, regularly monitoring and adjusting your information strategy is indispensable for its semipermanent success. You should:
- Compare the outcomes and your concern objectives
- Make indispensable adjustments to enactment aligned with evolving concern needs and marketplace conditions
- Ask users for feedback via Google Forms, Slack channels, oregon different survey tools
You'll request the close tools to guarantee your information is insightful, secure, and compliant.
Let's research the cardinal types of information strategy tools, from information absorption systems to analytics platforms and information solutions.
Data Management Tools
Image Source: Microsoft
Data absorption tools are the backbone of immoderate information strategy. They store, process, and negociate ample amounts of data.
This includes databases similar Oracle, a broad and wide utilized database strategy known for robust show and scalability. And Microsoft SQL Server, which offers a operation of precocious analytics and security.
Data absorption besides includes cloud-based solutions. Meaning businesses tin store and entree them implicit the internet. Popular solutions see AWS, Microsoft, and Panoply.
Data Analytics and Visualization Tools
Data analytics platforms assistance organizations portion and dice earthy information and crook numbers into trends and actionable insights. Like which products radical bargain the most, oregon which times of the twelvemonth are astir profitable.
Analytics platforms connection a scope of functions that let businesses to execute analyzable statistical analyses.
Data analytics platforms encompass wide concern analytics tools.
For example:
- SAP Analytics Cloud is simply a level that combines concern readying with dashboards, reporting, and predictive analytics
- Microsoft Power BI lets you consolidate information from antithetic sources and make reports, dashboards, and information visualizations
Marketing Analytics Tools
Market analytics tools play a cardinal relation successful your information strategy. They tin assistance you recognize selling performance, competitors, and, astir importantly, your customers.
For example, Market Explorer enables you to analyse immoderate market, place manufacture leaders and their acquisition channels, spot postulation trends, and cheque assemblage demographics.
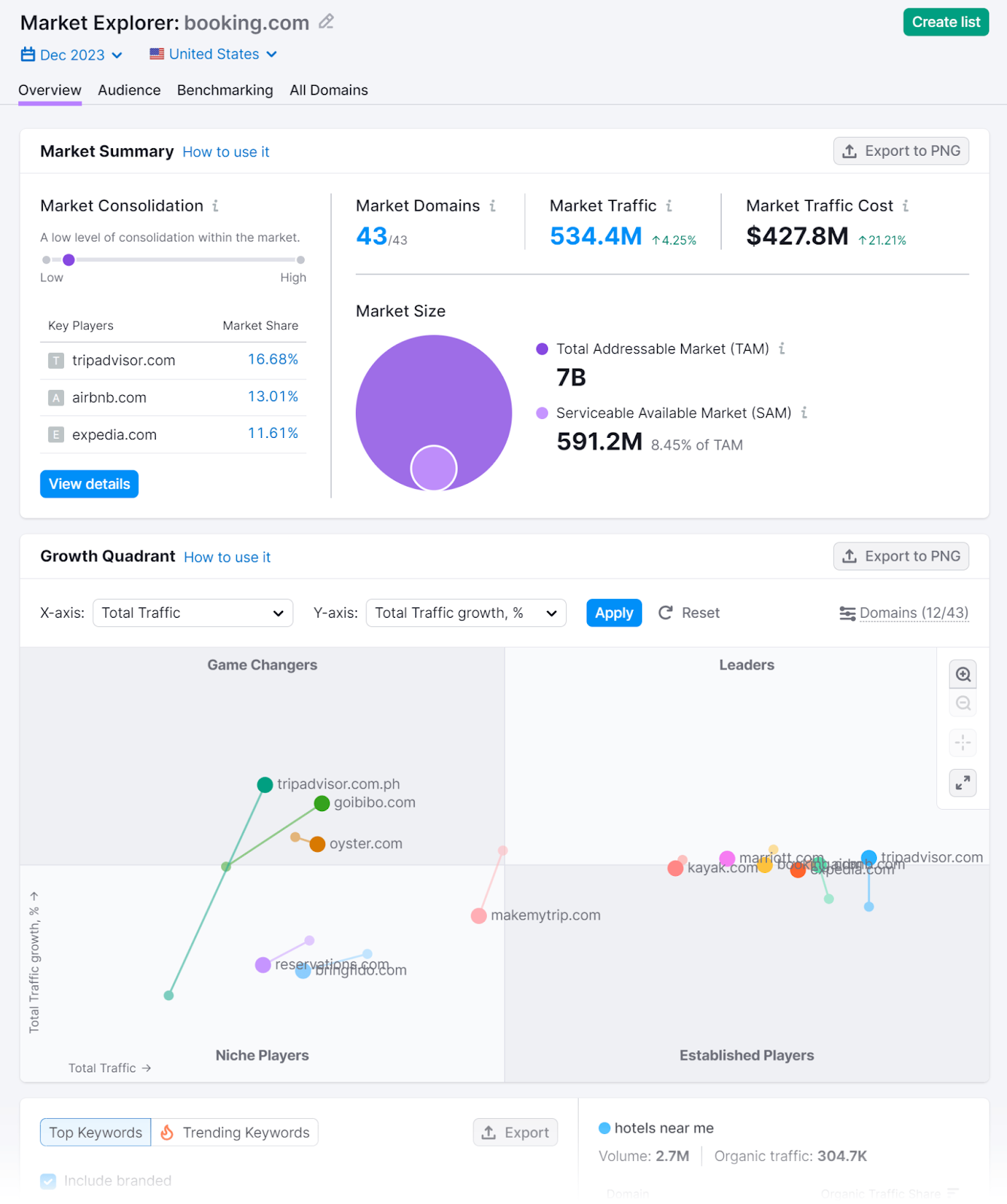
And a instrumentality similar Traffic Analytics volition supply information connected competitors' website traffic, including the fig of visitors and wherever they came from.
Google Analytics tracks and reports website traffic, providing insights into idiosyncratic behaviour and website performance.
Data Security Solutions
Security solutions support organizations’ information from unauthorized access, breaches, and different threats.
They see features similar encryption, intrusion detection systems, firewalls, and entree power mechanisms, providing a shield against hackers and cybercriminals.
Common cybersecurity solutions see Acronis for information backup, catastrophe recovery, and unafraid record sharing and Cohesity for information absorption to support companies against ransomware and more.
Successful Data Strategy Examples
Let’s research however immoderate starring companies person successfully implemented information strategies to recognize their customers and conscionable their needs better.
Netflix
Netflix uses information to connection highly personalized viewing experiences and determine which shows to put in.
The streaming level greets users by sanction erstwhile they unfastened the level and provides personalized recommendations connected the location screen. Netflix says these recommendations are based connected a user's viewing habits and the behaviour of akin users.
Netflix doesn’t conscionable urge shows users are apt to enjoy. Netflix besides personalizes galore aspects of the platform, including:
- Title cards and imagery
- Messaging
- Trailers
For example, Netflix created 10 versions of the “House of Cards” trailer to beforehand the show. Users who liked a circumstantial histrion successful the amusement were much apt to spot a trailer with them successful it, personalizing their viewing experience.
This tailored attack enables Netflix to amusement audiences the astir due shows for them successful the astir appealing way.
Starbucks
Starbucks’ rewards programme collects information to heighten lawsuit experiences and thrust loyalty.
Customers tin motion up for escaped and commencement collecting subordinate points (known arsenic stars) utilizing the Starbucks mobile app. This not lone encourages customers to devour much Starbucks products to cod points, but it besides gives the institution a ton of data.
Starbucks tin usage that information to:
- Send tailored offers via email and in-app propulsion notifications
- Monitor which locations are fashionable (and which aren’t)
- Engage with customers connected their birthdays
- Reach retired to customers who haven’t ordered successful a while
This each helps Starbucks foster marque loyalty and boost recurring sales.
Airbnb
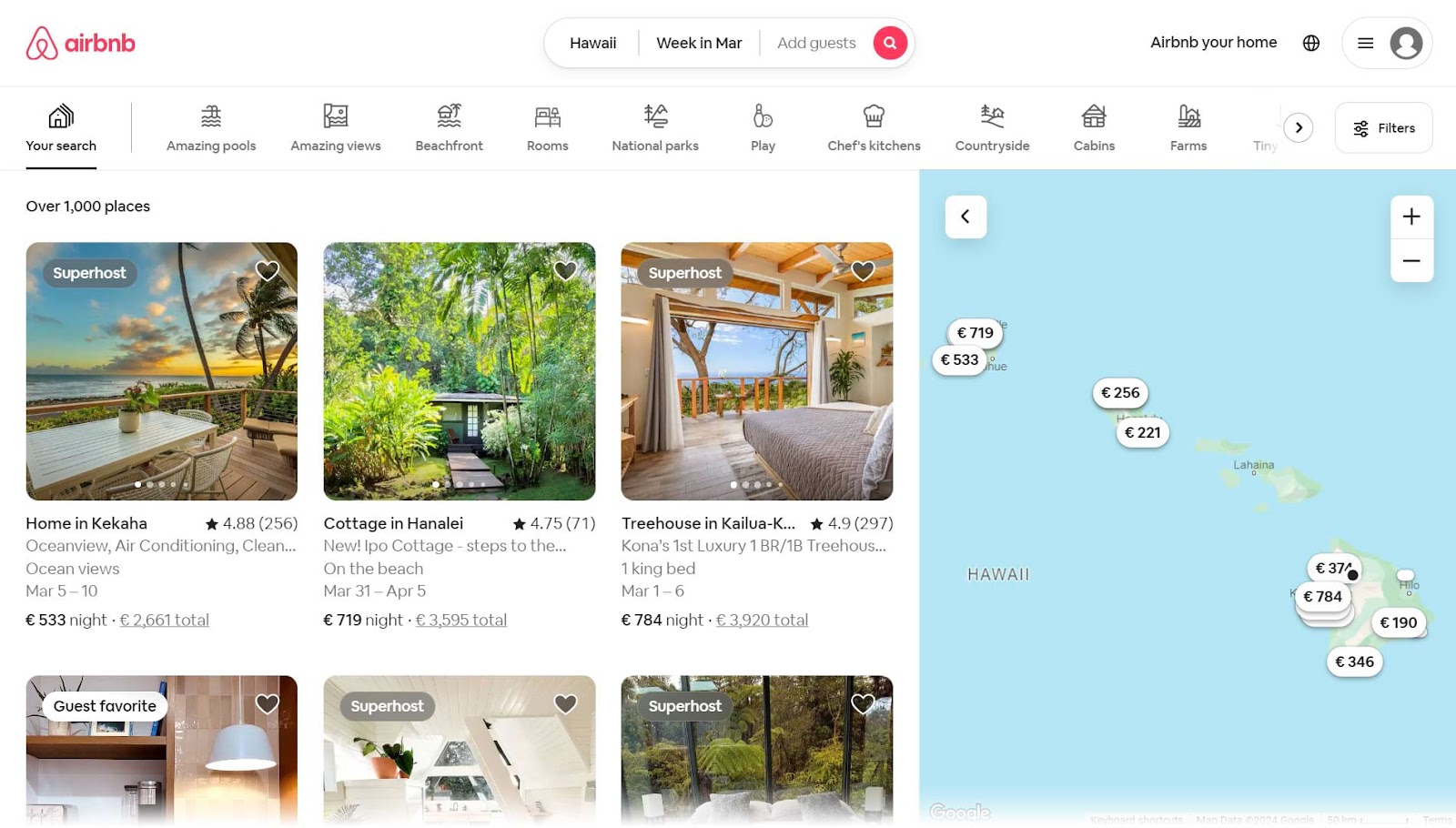
Airbnb is simply a person successful the hospitality industry. And it’s a large information strategy example. They usage information to summation the likelihood of guests uncovering a spot they’ll enjoy.
When a impermanent searches for accommodation, Airbnb uses instrumentality learning algorithms to lucifer guests with applicable listings. The hunt results leafage is fundamentally personalized recommendations based connected the places guests click on, the places they view, and big preferences.
This data-driven attack helps guests find determination they are apt to book. Which helps Airbnb thrust much bookings and blessed customers.
Create Your Own Powerful Data Strategy
Data is much than conscionable numbers and statistics. It's a invaluable plus that tin unfastened doors to caller opportunities, innovations, and growth.
In the epoch of large information and AI, the businesses that win volition beryllium those that not lone cod information but genuinely recognize however to usage it.
As you embark connected your information strategy journey, retrieve that wide objectives and the close tools are essential.
Try Market Explorer present and commencement collecting lawsuit insights to powerfulness your information strategy.









 English (US)
English (US)